Microsoft Entra ID is Azure's identity and access management (IAM) service. It lets you manage users and their permissions.
WinGet is Windows' new package manager. It lets you install and update applications from the command line. Since version 1.7.10582, WinGet supports Entra ID as an authentication provider. This lets private WinGet repositories such as winget.pro control access to applications on a per-user basis.
End user perspective
When a private WinGet repository requires Entra ID authentication, then many WinGet commands display the following message:
Additionally, Windows may bring up a dialog for signing in:
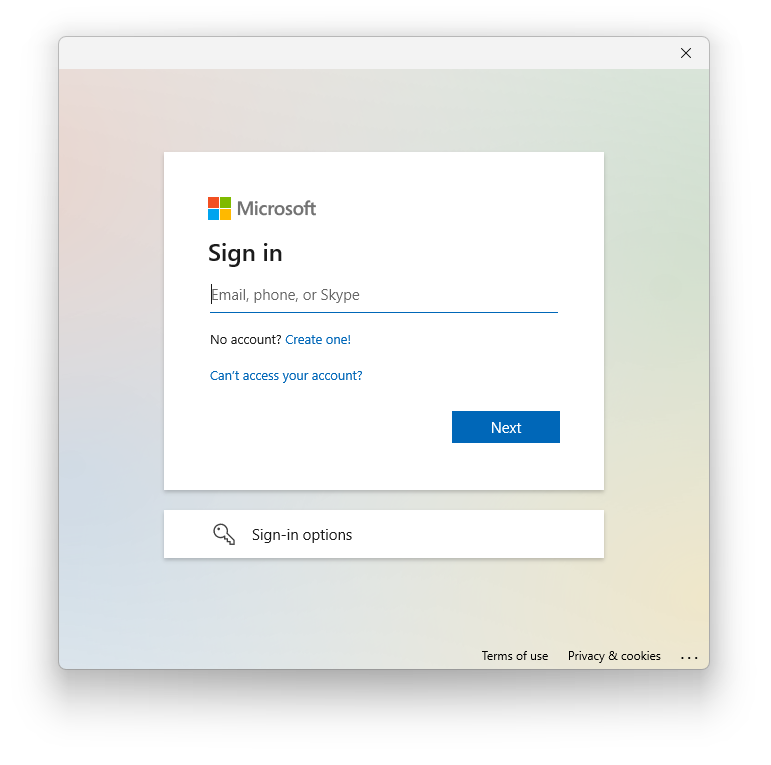
Once the user has signed in, the WinGet repository receives information about the user and can decide which applications to show.
Setting up Entra ID authentication in winget.pro
winget.pro lets you define which applications are available to which Entra ID users. To do so, open the application's page in the admin interface and enter the object IDs of the Entra users or groups that should have access.
As soon as you restrict at least one application in this way, winget.pro will require all users of the repository to authenticate with Entra ID. Out of the box, they will get the following error:
(The error message really contains those strange special characters.)
To fix the error, you need to look up your tenant ID under
Microsoft Entra ID in the Azure portal. It should be a UUID
such as 12345678-1234-1234-1234-123456789012. Then, open
the following URL in your browser:
https://login.microsoftonline.com/<your tenant id>/v2.0/adminconsent?client_id=23ce3c43-38b4-4d2e-b4da-a1fda3e2bc5b&scope=User.Read
Log in with your Azure admin account and grant the necessary permissions. Once you have done this, your users should no longer see the error above.
Warning
By default, applications are available to all users of the private winget.pro repository. This is also the case when the repository requires Entra ID authentication. If you do not want all of your users to see an application, then you need to restrict it to at least one Entra ID user.
REST API for managing allowed Entra ID users and groups
winget.pro has a REST API. It also lets you assign Entra ID users and
groups ("principals") to applications. You can explore the API in your
browser by logging in at
api.winget.pro/admin, then
navigating to
api.winget.pro/api/v1.
The following actions conveniently control which Entra ID users and
groups have access to an application with id <pk>
-
GET /api/v1/packages/<pk>/allowed-principals/: Get a list of Entra ID users and groups that have access to the application. -
POST /api/v1/packages/<pk>/allowed-principals/: Add an Entra ID user or group to the application. The request body should be a JSON string. -
PUT /api/v1/packages/<pk>/allowed-principals/: Set the complete list of Entra ID users and groups that have access to the application. The request body should be a JSON list of strings. -
DELETE /api/v1/packages/<pk>/allowed-principals/<principal>: Remove the given user or group from the list of Entra ID users that have access to the application.
In all cases, Entra ID users and groups are identified by their object
ID. This is a UUID such as
12345678-1234-1234-1234-123456789012.